
Interview with a SOC 2 auditor: Mistakes to avoid during SOC 2 Type II
Emily Bonnie
Senior Content Marketing Manager
Experts predict that cybersecurity will cost the world nearly $6 trillion by the end of 2021.
As the number of cyber threats increases, any service organization that manages users’ confidential information must have proper security controls and standards in place. Here’s where SOC reports come into play, especially SOC 2.
If you’re planning to get a SOC 2 audit soon, you should start by exploring the common mistakes organizations make with this type of examination. To help you, we interviewed K.C. Fikes, Data Analytics Practice Lead at The Cadence Group. We asked him seven questions that can help you better prepare for your SOC 2 audit. More specifically, we focused this interview on SOC 2 Type II audits.
Let’s start with a basic question.
1. Can you give a brief intro to SOC 2?
SOC 2 audits help service-based organizations ensure they have the right internal controls to process, manage, share, and protect the sensitive information of clients and their customer data.
For example, if you provide HR management services, you should protect information from not only the companies using you serve but also the data that is directly or indirectly related to that service (e.g., candidates’ information submitted through a job application form).
How does a SOC 2 audit work?
In the words of Fike: “SOC 2 Type II is a report in which a CPA firm has come in and audited your controls (as they relate to the Trust Services Criteria in scope) for a specific period (e.g., 12 months).”
As you can see, the Trust Principles established by the AICPA are crucial for SOC 2. These principles include:
- Security: Controls that help you protect your clients’ information against unauthorized access (e.g., firewalls and authentication standards).
- Availability: Controls and standards that define how accessible your information is to clients (e.g., performance monitoring).
- Processing integrity: Controls that help you provide reliable, timely, and accurate information to your clients (e.g., continuous quality assurance procedures)
- Confidentiality: Processes you have in place to handle clients’ confidential information (e.g., permission levels).
- Privacy: Controls and processes that ensure your clients’ Personal Identifiable Information (PII) stays private (e.g., name, social security number).
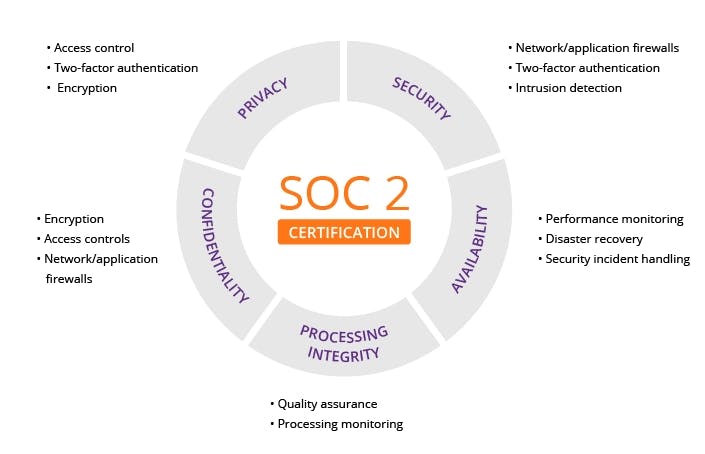
The sum of all these processes makes up the operational system that helps you protect clients’ data most effectively.
That said, to get your SOC 2 certification, you only need to comply with the “Security” principle. That’s why it’s often referred to as “Common criteria.”
2. Can you explain the auditing process?
Now that you understand what SOC 2 reports are, the question becomes: How does the auditing process work from the auditor’s perspective?
Fike explains, “Assuming you’re type II, we’ll come in a couple of weeks before the period of review ends. We’ll do a kickoff and talk to the key players and request populations (e.g., each instance of some sort of technology function operating, like a software change or security monitoring software logs).
“From the populations, we’ll sample some of them to see if the internal control was working. For example, we might sample 10 of the 100 software changes during the review period and see if they were peer-reviewed.
“We test each sample against each control. Once we’re done assessing, and if everything checks out, then we’re done. We go and write the report. If we sampled something and didn’t meet the attribute of a control, we go to the company and see what happened. We tell the client that we’re missing something and look for any evidence that proves this sample meets controls.
“Then, we’ll look at the sample that didn’t pass, and we’ll potentially expand the samples to analyze whether it was just an outlier or a systemic issue. If it was an outlier, we would note an exception. If it wasn’t an outlier, we might go so far as to say it was a failure of the control. Our reports would note these exceptions and failures.”
In other words, the process can be divided into four main stages:
- Request populations: Collate instances of crucial functions in operation
- Test samples: Test samples for each control
- Test failed controls: Test failed controls to look for outliers assess operating effectiveness
- Issue report: Issue report with exceptions and failures opinion and results of control testing
3. What are the requirements of SOC 2?
As we stated a bit earlier, SOC 2 examinations are based on the five Trust Principles defined by the AICPA.
Depending on your industry, service, and regulations, the auditor will “map” your controls according to the principles that better adapt to your specific situation.
Fike described two stages in which an auditor performs this process:
- Mapping: “We map controls to each of the TSC. Usually a one-to-many match (one trust service to multiple controls).”
- Testing: “We test those controls and then go into the auditing process.”
- Reporting: “We issue an opinion within the report based on mapping, controls, testing.”
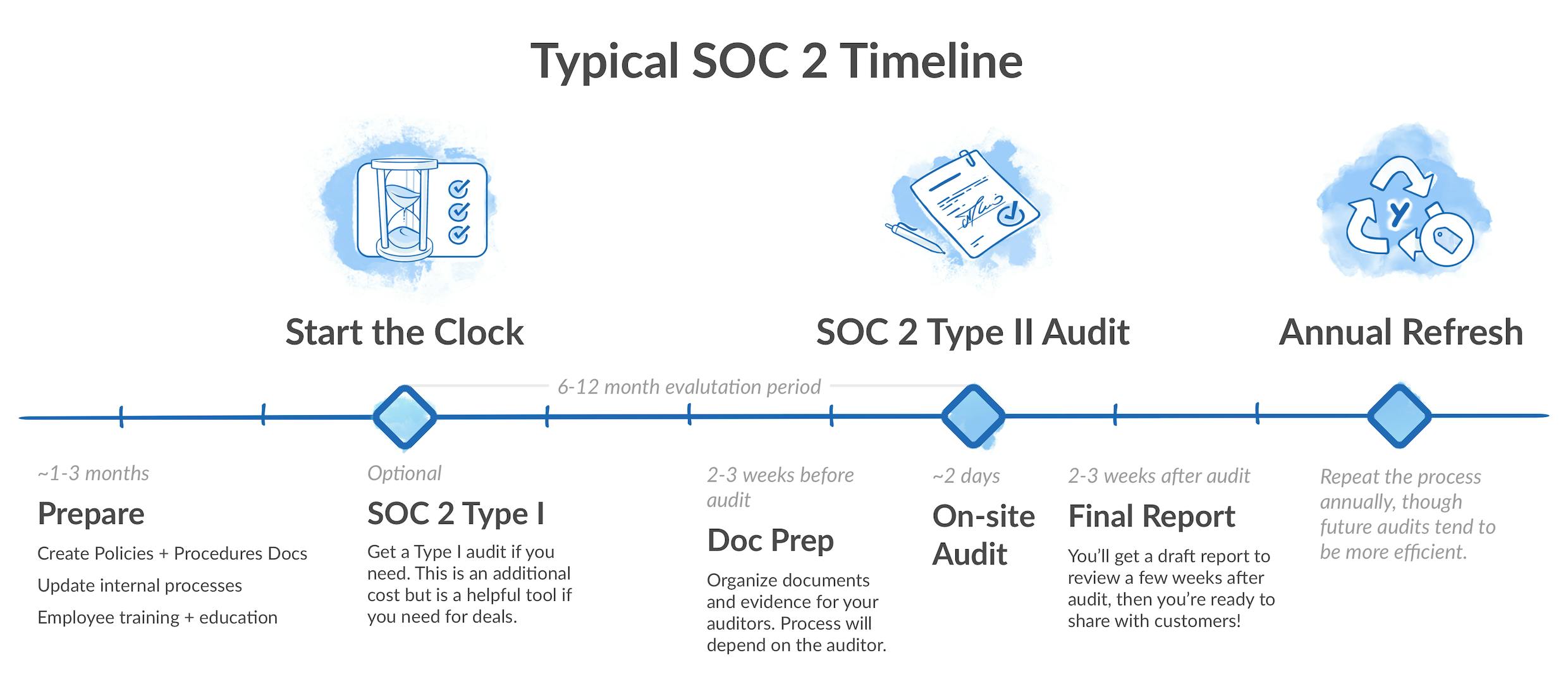
The scope of this process can vary depending on different factors and can take anywhere from 6 to 12 months. With Secureframe, we can do it within 4-6 weeks
4. What common mistakes do companies make during SOC 2 audits?
By exploring what other organizations have done wrong and avoiding those mistakes, you’re able to save time and get your SOC 2 report much faster.
To help you with this, we asked Fike about the common mistakes organizations make during a SOC 2 audit.
He provided five main mistakes:
- “No control ownership (e.g., control owners uncertain on what their responsibilities are)”
- “No defined scope (e.g., applications and/or infrastructure you have in place for the SOC 2 audit)”
- “No readiness project performed”
- “Controls stop operating”
- “Processes or technology changes where controls don't match/meet"
If I had to choose “the top” mistake from this list, though, I’d select “Not performing a readiness assessment prior to your examination.”
As the term suggests, a readiness assessment helps you find out how ready you are for a SOC 2 audit. It helps you test your controls and find potential issues before the auditor comes into your organization. This way, you can fix any problems and make sure all your controls are working properly. Once the auditor starts analyzing your performance, you’ll be better prepared.
Fortunately, most CPA firms with some experience with SOC examinations can perform this kind of analysis and help you mitigate any risk involved.
5. How can companies avoid these common mistakes?
At this point, you already understand the main mistakes and blunders organizations make during SOC 2 audits, but how can you avoid them?
Here’s what Fikes suggests:
- “Defining an owner or someone in charge of the controls and sending out marching orders for the controls.”
- “Doing periodic tests of the controls, like a pseudo internal audit.”
- “Organizational awareness of SOC 2 and security culture.”
The last one is especially important. Security is always a collaborative effort.
If your entire organization doesn’t understand the value of implementing the information security practices you have in place, you’ll struggle with adoption. By developing a solid security culture in your business, you’ll avoid many of the pitfalls and mistakes described earlier.
6. How can companies prepare for a SOC 2 audit?
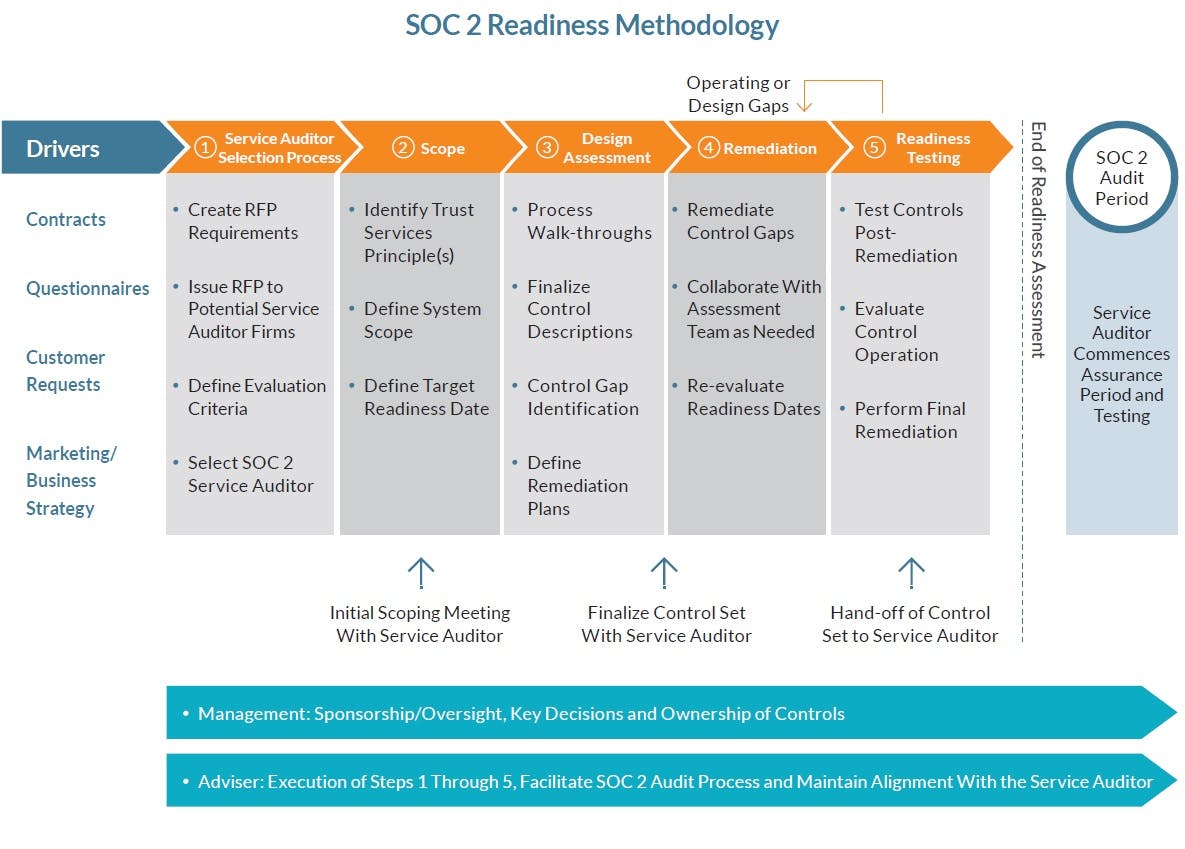
Again, the best way to prepare for a SOC 2 examination is by performing a readiness assessment. This type of assessment helps you discover what you’re doing right and wrong and fix any issue prior to the audit.
In the words of Fikes:
“Readiness projects are great because they are true assessments of a brand new environment. If companies are new to controls, this is a helpful way to start, as it helps you “demystify the controls.”
7. Any final thoughts?
Getting the input of an auditor is pretty useful, as it gives you the perspective of someone who truly understands the process.
That’s why we asked Fikes for three last tips to help you prepare for a SOC 2 audit. Here’s what he answered:
- “Control ownership and expectation of control management”
- “Having a project management system in place”
- “Senior management buy-in from the top down is key to success”
Ready to get your SOC 2 Type II certification?
SOC 2 Type II certifications come with several benefits, including:
- Mitigating risks and preventing potential data leaks and security issues
- Positioning your organization as reliable, compliant, and trustworthy
- Increasing your own security and standardizing crucial processes
- Finding continuous improvement opportunities
- Building more trust with clients and prospects by making them feel more secure
Hopefully, you now have a better understanding of what auditors look for during a SOC 2 audit, as well as how to prepare for your audit process.
And, if you’re looking for a faster, better way to achieve SOC 2 compliance, then Secureframe can help. We help organizations streamline their security processes and get audit-ready in weeks, not months.
To learn more, check out our product overview page.

Emily Bonnie
Senior Content Marketing Manager
Emily Bonnie is a seasoned digital marketing strategist with over ten years of experience creating content that attracts, engages, and converts for leading SaaS companies. At Secureframe, she helps demystify complex governance, risk, and compliance (GRC) topics, turning technical frameworks and regulations into accessible, actionable guidance. Her work aims to empower organizations of all sizes to strengthen their security posture, streamline compliance, and build lasting trust with customers.