
Interview with a SOC 2 Auditor: What Does an Auditor Look for During the Audit?
Emily Bonnie
Senior Content Marketing Manager
If you’re a service-based company, becoming SOC 2 compliant is an important step.
With the increasing number of cyber threats, clients feel more comfortable with a business that goes through this type of examination.
But if you’re reading this guide, chances are you already know that.
Now the question becomes: What can you do to prepare for a SOC 2 audit?
To help you out, we interviewed auditor K.C. Fikes, Data Analytics Practice Lead at The Cadence Group.
He answered some of our most frequently-asked questions.
But let's start out with our own quick primer on SOC 2 audits.
What is a SOC 2 audit?
SOC 2 audits analyze the operations and controls of service-based organizations in terms of the Trust Services Criteria outlined by the AICPA (American Institute of Certified Public Accountants), which include:
- Security (often referred to as “common criteria”): Controls you have to protect confidential data from unauthorized access.
- Availability: Controls that help you make sure your services are available to clients, employees, and customers when they need them.
- Processing integrity: Standards you have in place for your processing system (i.e., how are you making sure your systems provide timely, accurate data to clients?)
- Confidentiality: Controls and standards that help you manage, classify, access, and protect clients’ confidential data.
- Privacy: Controls you’re using to keep your clients’ sensitive information private.
Here's a quick diagram of how it all fits together:
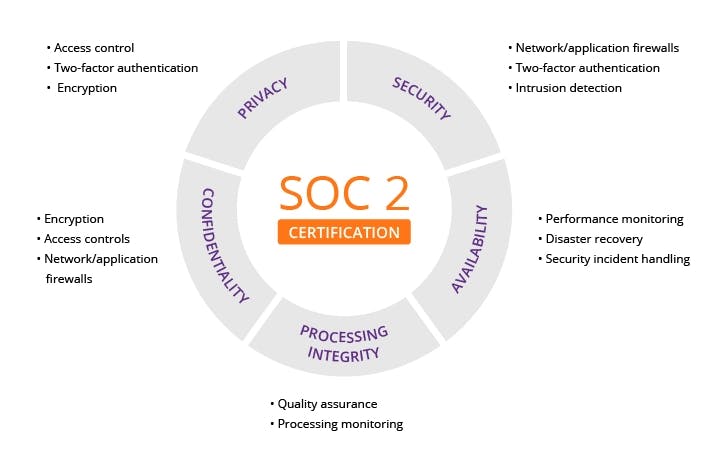
All these principles working together help you effectively protect customer data. The only required criteria to become SOC 2 compliant is security, best known as “common criteria.”
That said, the best way to understand SOC 2 audits is by “getting into the mind” of an actual auditor.
So we asked one.
What do you look for when examining an organization?
“Assuming you’re type II, we’ll come in a couple weeks before the period of review ends. We’ll do a kick off and talk to the key players and request populations (e.g., instances of some sort of technology function in operation, like a software change or security monitoring software logs).
“From the populations, we’ll sample some of them to see if the control was working. For example, we might sample 10 of the 100 software changes during the review period and see if they were reviewed by peers.
“Then, we’ll test each sample against each control.
“After this assessment, if everything worked out correctly, we will start writing the report.”
But what happens if one of your controls isn’t working properly?
“If we sampled something and didn’t meet the attribute of a control, we go to the firm and see what happened. We tell the client that we’re missing something. Is there any evidence for this sample to meet controls? Then, we’ll look at the sample that didn’t pass. We might also expand the samples to analyze whether it was just an outlier or see if there’s more of a systemic issue.
“If it was an outlier, we note an exception. If it wasn’t, we might say it was a failure of the control. Our reports would note these exceptions and failures.”
To get a more thorough explanation of SOC 2 audits, we suggest you read our complete guide to SOC 2.
How long does an audit take?
SOC 2 audits can be split into two main types: Type I and Type II.
The length of your audit will depend on the report type you’re looking for.
Here is the average scope for each report provided by K.C. Fike:
- Type I: About a month and a half.
- Type II: A couple weeks longer. From kick-off to handing in the report, it’s about two months.”
If this is the first time you’re going through a SOC 2 assessment, we suggest you start with a SOC 2 Type I report, as they’re simpler audits that can help you prepare for a Type II report.
What are the differences between Type l and Type ll reports in a SOC 2 audit?
The main difference between SOC 2 Type I and SOC 2 Type II lies in the length of each.
SOC 2 Type I reports analyze the performance of your controls at a single point in time (e.g., SOC 2 report for May 15, 2021).
SOC 2 Type II reports analyze the performance of your controls over a longer period (e.g., SOC 2 report of May 15, 2021, to July 15, 2021).
Fikes also mentions other crucial differences between each report type, breaking them down piece by piece.
According to Fikes, these reports consist of the following:
Type I
- Auditor‘s opinion
- Client’s opinion
- Narrative
- Mapping of the controls to TSC
Type II
- Auditor’s opinion
- Client’s opinion
- Narrative
- Mapping of the controls to TSC
- Management’s response
Our SOC 1 vs. SOC 2 guide provides a more detailed explanation of all the elements involved in the different report types. It’s a great way to deepen your understanding of this topic.
Which specific controls do companies typically have difficulty passing?
Understanding the overall guidelines to become SOC 2 compliant is important, but what about the most common challenges?
Fikes suggests you pay special attention to the following controls, as organizations often struggle with them:
- Non-usual controls: “Those controls that don’t operate as frequently as others because those get forgotten (e.g., forgetting to do annual risk assessments or annual reviews).”
- Unclear controls: “Controls that don’t have clearly defined policies or procedures (e.g., getting a lot of data from a logging tool but not knowing how to properly respond).”
“It’s important to have very clear organizational management on how to deal with controls.”
What are the primary red flags you look for during an audit?
Here’s where it gets interesting.
As Mark Grey states: “A team is only as strong as its weakest people.”
In the same way, your SOC 2 compliance will depend not on your best controls but your weakest.
The best way to prepare for a SOC 2 examination is by analyzing your controls and identifying which are the least efficient. That’s where you should put most of your attention.
To help you out, Fikes laid out some primary red flags you should be careful of:
- Responsibilities: “No control ownership (e.g., control owners uncertain on what their responsibilities are).”
- Scope: “No defined scope (e.g., what applications/infrastructure do you need for a SOC 2 assessment?).”
- Readiness assessment: “No readiness project performed.”
- Lack of preparation: “Controls stop operating.”
- Inconsistencies: “Processes/technology changes but controls don’t match/meet.”
By paying attention to these elements, you’ll be better prepared for your SOC 2 audit.
Also, it’s especially important to perform a readiness assessment prior to your examination. This way, you’re able to spot potential issues with your controls and fix them before the auditor comes in to analyze your firm.
Lack of preparation is one of the main reasons organizations don’t pass a SOC 2 audit.
Do you have any last words for companies preparing for a SOC 2 audit?
At this point, you already understand the basics of becoming SOC 2 compliant.
To help you become more prepared, we asked Fikes for some extra tips to consider.
Here’s what he said:
- “Have a clear idea of how you manage the compliance process.”
- “Define an owner or person in charge of handling compliance at scale.”
- “Have a budget to make security a priority for resources, tools, and personnel.”
- “Make sure there’s true buy-in from senior management from the top.”
The last one is especially crucial.
If management doesn’t truly support your security compliance, you’ll experience tons of issues during the whole process.
A SOC 2 assessment should be completely aligned with business objectives and goals.
We suggest you schedule a meeting with your management team to discuss all the benefits that come with a SOC 2 examination and make sure they’re fully on board with the process.
Are you ready for the SOC 2 attestation process?
SOC 2 examinations help service-based organizations ensure they have the best controls in place to protect a client’s confidential data.
By becoming SOC 2 compliant, you’re able to protect one of your most valuable assets: data.
Hopefully, the answers provided today can help you better prepare for your examination and start off on the right foot.
And, if you need more thorough guidance for your security compliance, Secureframe might be able to help. To see for yourself, read our product overview page to learn more about our process.

Emily Bonnie
Senior Content Marketing Manager
Emily Bonnie is a seasoned digital marketing strategist with over ten years of experience creating content that attracts, engages, and converts for leading SaaS companies. At Secureframe, she helps demystify complex governance, risk, and compliance (GRC) topics, turning technical frameworks and regulations into accessible, actionable guidance. Her work aims to empower organizations of all sizes to strengthen their security posture, streamline compliance, and build lasting trust with customers.