9 Secureframe Dashboards for Complete, Real-Time Visibility Into Cybersecurity and Compliance
Emily Bonnie
Senior Content Marketing Manager
Rob Gutierrez
Senior Cybersecurity and Compliance Manager, CISA, CCSK, CMMC RP
Imagine you're trying to keep your house safe from intruders. You have locks on your doors, an alarm system, and maybe even cameras. But if you can't see what's happening inside your house, you might miss signs that something's wrong, like an open window or broken door latch.
In the same way, getting visibility into your cybersecurity and compliance posture is about being able to see everything that's going on in your systems and networks so you can keep your sensitive data safe. But actually achieving that visibility can be a major challenge:
- Complexity: Growing companies have a multitude of devices, applications, personnel, and vendors. Keeping track of all these elements and ensuring they’re secure can be incredibly complicated.
- Constantly changing threats: Cyber threats are always evolving, making it difficult to keep up and know where to look for weaknesses.
- Volume of data: There’s a massive amount of data flowing through a company’s network every second, making it difficult to separate signals from noise.
- Lack of integration: Companies often use different tools for different parts of their security and compliance efforts, making it difficult to get a complete, up-to-date picture of your control environment and compliance status.
- Resource limitations: Not every company has the resources to hire a team of cybersecurity experts. Smaller teams are asked to do more with less.
- Regulatory requirements: Regulatory compliance can be a moving target. Different rules apply to different industries and regions, and regulatory requirements change and evolve in response to the threat landscape.
Using a GRC platform like Secureframe gives you the visibility you need to see and understand what's happening across all these areas, so you can stay proactive and resilient in the face of cybersecurity challenges. You’ll be able to pinpoint vulnerabilities before they can cause significant damage, act swiftly to identify and mitigate risks, and avoid regulatory fines and non-compliance issues.
9 Secureframe cybersecurity dashboards for enhanced visibility and stronger security and compliance
In a customer survey conducted by UserEvidence, over half of Secureframe users said poor visibility into control status and overall security posture was one of the main reasons they invested in a GRC tool. 57% cited the lack of a centralized, single source of truth in storing and managing security and compliance data as their main challenge. After using the platform, 97% of them also said they would recommend Secureframe to colleagues.
Let’s explore nine cybersecurity dashboards our customers find particularly valuable in gaining visibility across their security and compliance programs.
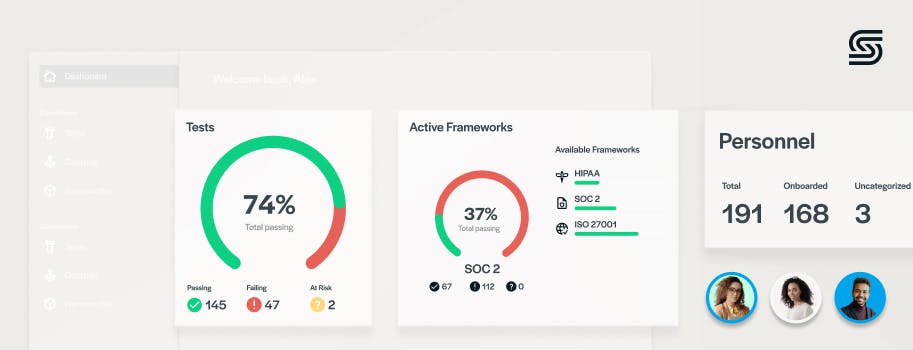
1. Security and compliance status overview
A centralized security and compliance dashboard consolidates your most vital security metrics and compliance-related information into a single screen, making it easier for security teams, compliance officers, and other stakeholders to understand the current state of your organization's security and compliance posture.
Secureframe consolidates all of your most important security and compliance metrics into a single view when you first log into the platform, including overall system health and control status, regulatory compliance status, any compliance gaps, and more. Armed with this real-time snapshot, organizations can quickly gauge their overall security and get immediate visibility into vulnerabilities, threats, and compliance gaps.
In addition, all of the data within the Secureframe platform is fully exportable, so the information within these dashboards can be easily shared for executive reporting, audit documentation, or to share detailed compliance information with other stakeholders.

2. Risk register
A risk register is like a master list of all the potential threats, vulnerabilities, and risks facing your business. With all your risks organized in one place, you’ll be able to prioritize them, plan ahead to prevent or minimize their impact, and assign ownership of each risk to make sure nothing gets overlooked. You’ll also be able to clearly communicate with stakeholders what the highest priority risks are, what’s being done about them, and make decisions based on a clear understanding of potential risks and their impact. It all leads to more strategic and less reactive decision-making.
With Secureframe, you can quickly build your risk register using templated risks from our risk library, by creating custom risks, or by importing your existing risk register as a CSV. After importing a risk description from the risk library or entering your own risk details and assigning an owner, you can leverage Comply AI for Risk to automatically fill in most fields in the risk assessment workflow — including a risk score, justification, treatment, and more. At the end of the workflow, you can review and validate the output to ensure accuracy.
This feature not only saves you valuable time and resources but also ensures that each risk is reported consistently and repeatably. You won’t need to spend time assigning categories or performing risk analysis calculations.
The Secureframe risk register is easy to update and view at a glance, allowing your organization to stay aware of and assess risks as they change, review treatment and remediation plans, and continually improve its risk management processes.

3. Risk history and trends
Risk trend reports compile data about your risks and display it in a way that's easy to understand. They highlight how certain risks have evolved, emerging trends that might indicate a growing threat or opportunity, and whether the severity or probability of specific risks are increasing or decreasing.
Understanding which risks are trending up or down helps you prioritize where to focus your efforts and resources. You can concentrate on high-impact areas without wasting time on risks that aren't changing much. Plus, regularly reviewing risk trends allows you to continually refine and improve your risk management practices.
Secureframe’s risk dashboards provide that essential, holistic view of your organization’s risks. You can visually monitor your progress over time with heat maps, summary tables, and trend charts. These graphs make it easy to identify escalating threats, communicate high-priority risks, highlight areas where you’ve made improvements, and clearly demonstrate the overall health of your risk management program to executives, auditors, and other stakeholders.

4. Compliance status dashboard
Managing compliance can be complex, with dozens of moving parts. Compliance dashboards bring all of your compliance data together in one place to give you a clear, real-time overview of where you stand with the frameworks applicable to your business.
With a clear view of deadlines and tasks, you can stay organized, informed, and prepared instead of scrambling right before an audit. Monitoring your real-time compliance status also allows you to quickly spot and proactively address potential gaps before they become major issues.
Secureframe’s Frameworks page displays a real-time picture of your compliance status across your selected security standards and regulations. Because Secureframe integrates with your tech stack, it can assess implemented controls mapped to specific frameworks like SOC 2, ISO 27001, HIPAA, PCI, NIST 800-53, and dozens of other standards (as well as custom frameworks).
This dashboard not only gives you immediate visibility into your current compliance status, it also flags any failing controls. This makes it significantly easier to proactively address any non-compliance issues as they occur, rather than discovering them during preparation for point-in-time audits. From this dashboard, you can also click into specific requirements and controls for a given framework. You can easily review passing and failing controls organized by type and assign them to the appropriate owner from a single screen.
These dashboards also reflect progress toward compliance with new frameworks, with a clear picture of what’s already been accomplished and how much is left to be done. This dashboard also makes it easy to track how closely you’re adhering to regulatory requirements throughout the year to avoid non-compliance violations and penalties.

5. Vulnerability management dashboard
Vulnerability management dashboards are essential tools that help you stay on top of potential security risks. They display a real-time overview of vulnerabilities across your systems, applications, and network, making it easier to prioritize and address them before they can be exploited. Instead of juggling spreadsheets and emails, everything you need to know about open vulnerabilities is in one place so you can manage remediation tasks and track your efforts.
Many security standards and regulatory frameworks also require regular vulnerability assessments. Dashboards help you stay compliant by scanning your tech stack, identifying vulnerabilities and misconfigurations, and providing the necessary documentation to demonstrate your efforts to address them to auditors and other stakeholders.
The Vulnerabilities Tab in Secureframe simplifies vulnerability management by pulling in data from cloud platforms and developer tools like AWS Inspector and Github Dependabot to give clear visibility into vulnerabilities from multiple resources in a single view. Common Vulnerabilities and Exposures (CVE) data is automatically pulled from these connected integrations to automatically alert you when vulnerabilities are discovered — with no agent required. From there you can assign control owners as well as create and assign JIRA tickets for remediation tasks.

6. Third-party risk and compliance dashboard
98% of organizations have vendor relationships with at least one third party that has experienced a breach in the last two years.
When you partner with a third-party vendor, you're not just sharing a project — you're potentially sharing sensitive data and access to your systems. It’s critical to ensure that the vendors your business works with are secure and compliant.
If a vendor has weak security practices, it can create vulnerabilities that could be exploited, putting your entire business at risk. By assessing their security posture, you ensure they're meeting your standards and not exposing you to unnecessary risks.
Compliance is equally important. Different industries have specific regulations to protect data and ensure ethical practices. If your vendor isn’t compliant, it could lead to legal issues or hefty fines for your business.
But getting clear visibility into their security practices and compliance status is a major challenge. By centralizing and automating third-party review and risk management processes, Secureframe not only saves time but also strengthens your organization’s ability to prevent third-party data breaches and maintain compliance.
Secureframe TPRM provides a centralized tool where you can access a comprehensive inventory of all third parties your organization uses, including vendors, suppliers, contractors, partners, software providers, open source projects, and other external entities. The Vendors tab offers access to an inventory containing both active and archived vendors, complete with their risk levels. Each vendor profile provides detailed information about services and security compliance, including authentication methods and audit results, ensuring comprehensive vendor oversight.
Admins can also evaluate a vendor’s risk based on the data and environments they access, and all relevant documents including compliance reports and policies, can be attached to the vendor’s profile for easy access. This ability to review compliance documents, security attestations, and reports makes it easier to perform effective third-party risk assessments.


7. Vendor access dashboard
When your employees access different vendors, they could be sharing sensitive information or connecting to external systems that might not be as secure as yours. By tracking vendor access, you can ensure that no unnecessary risks are being introduced, as well as spot any unusual activity that could indicate a security issue.
This kind of monitoring also helps you manage costs and improve efficiency. If you see that multiple individuals or teams are accessing different vendors for the same service, you might find opportunities to streamline and cut expenses.
Secureframe’s Vendor Access dashboard makes it easier to implement and enforce best practices like the principle of least privilege and periodic access reviews. With this dashboard, you can monitor the level of access each employee has to third-party vendors from a single screen. You can easily track and review individual employee access to specific apps, including their role, privilege status, 2FA, and SSO status — as well as monitor offboarded employees to ensure their access is removed. Secureframe also auto-detects unauthorized applications and vendors accessed by employees through Single Sign-On to prevent shadow IT.

8. Asset inventory dashboard
An asset inventory is a detailed list of all your company's physical and digital assets, like computers and software. When you know exactly what assets you have, who has access to them, and how they’re configured, it’s much easier to keep them secure. Plus, many security frameworks and regulations require businesses to have detailed records of their assets.
Secureframe provides a single view for you to track and manage employee computers, cloud resources, and code repositories by automatically pulling information from your integrations, like endpoint management platforms, Cloud Service Providers (CSP), and version control tools.
Our Asset Inventory gives you a filterable view of the status of your organization’s assets. You can quickly understand which assets are critical for compliance and the potential risks they face so you can proactively protect your business.
- Quickly see which devices have fallen out of compliance. Get a granular view of an individual’s computer and if they have encryption, screen lock, and a firewall set up to meet compliance requirements.
- Use filters to customize your view of assets and resources
- Inventory, monitor, and control which cloud resources are in scope for an audit
- Configure in-scope version control repositories and include flags for specific requirements such as emergency changes and static code analysis testing. Easily track repos, manage branches, and view pull requests from the central code base.
- Assign task owners to ensure compliance issues are resolved quickly


9. Personnel dashboard
A personnel dashboard gives you a clear, real-time view of your employees’ compliance with security protocols and regulations. It helps you monitor training and background check completion, access permissions, and adherence to policies. If someone hasn’t completed mandatory training or if their access to sensitive data isn’t properly managed, the dashboard flags the issue so you can address it right away.
Secureframe’s Personnel dashboard makes it easy to track, manage, and maintain compliance among your employees and contractors, whether your company spans 10 or 10,000 personnel. The platform automatically imports personnel data through deep integrations with your HR, SSO, MDM, and other tools. When personnel depart your organization you can easily offboard them, revoke access to company systems and data, and mark them as ‘Out of Scope’ to avoid confusion during your audit.

Key takeaways for implementing effective cybersecurity dashboards
Cybersecurity dashboards are essential tools for organizations to enhance their security and compliance posture. They provide real-time visibility into critical aspects of your security landscape, from tracking vulnerabilities and monitoring compliance to managing third-party risks and maintaining a comprehensive asset inventory.
Implementing the right mix of dashboards for your organization's specific needs can lead to significant improvements in security oversight and risk management. Whether it's a risk register to track and manage potential risks, a compliance readiness dashboard to stay ahead of requirements, or a personnel dashboard to ensure your team is aligned with security protocols, these tools collectively contribute to a robust cybersecurity posture.
Ultimately, the goal is to create a cohesive and transparent security environment where threats are detected early, responses are swift and effective, and compliance is maintained effortlessly.
By adopting a tool like Secureframe, organizations can build a resilient defense against ever-evolving cyber threats, maintain continuous compliance, and build trust with customers and partners.
Use trust to accelerate growth

Emily Bonnie
Senior Content Marketing Manager
Emily Bonnie is a seasoned digital marketing strategist with over ten years of experience creating content that attracts, engages, and converts for leading SaaS companies. At Secureframe, she helps demystify complex governance, risk, and compliance (GRC) topics, turning technical frameworks and regulations into accessible, actionable guidance. Her work aims to empower organizations of all sizes to strengthen their security posture, streamline compliance, and build lasting trust with customers.

Rob Gutierrez
Senior Cybersecurity and Compliance Manager, CISA, CCSK, CMMC RP
Rob Gutierrez is an information security leader with nearly a decade of experience in GRC, IT audit, cybersecurity, FedRAMP, cloud, and supply chain assessments. As a former auditor and security consultant, Rob performed and managed CMMC, FedRAMP, FISMA, and other security and regulatory audits. At Secureframe, he’s helped hundreds of customers achieve compliance with federal and commercial frameworks, including NIST 800-171, NIST 800-53, FedRAMP, CMMC, SOC 2, and ISO 27001.