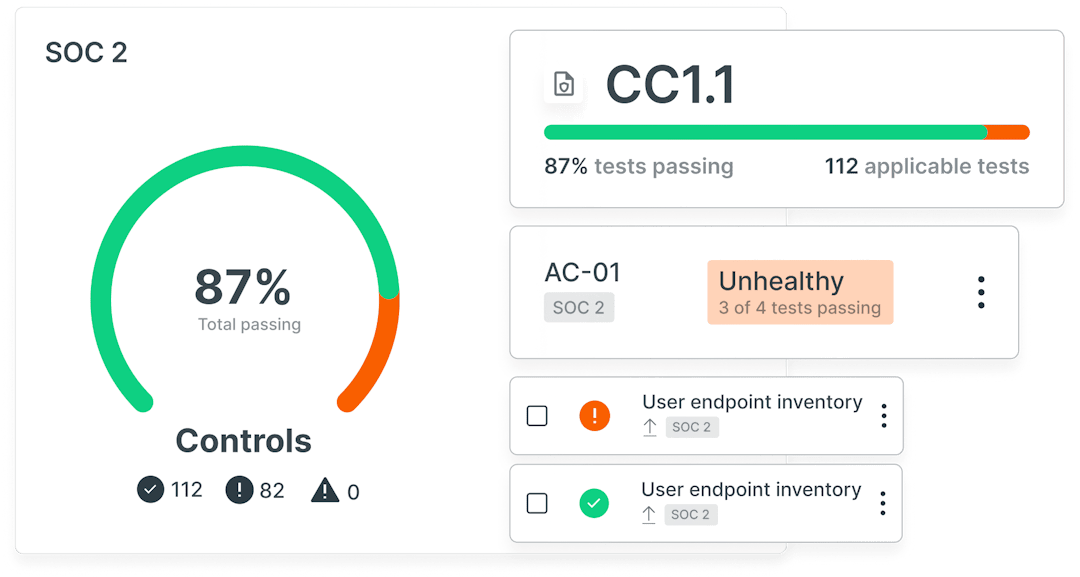
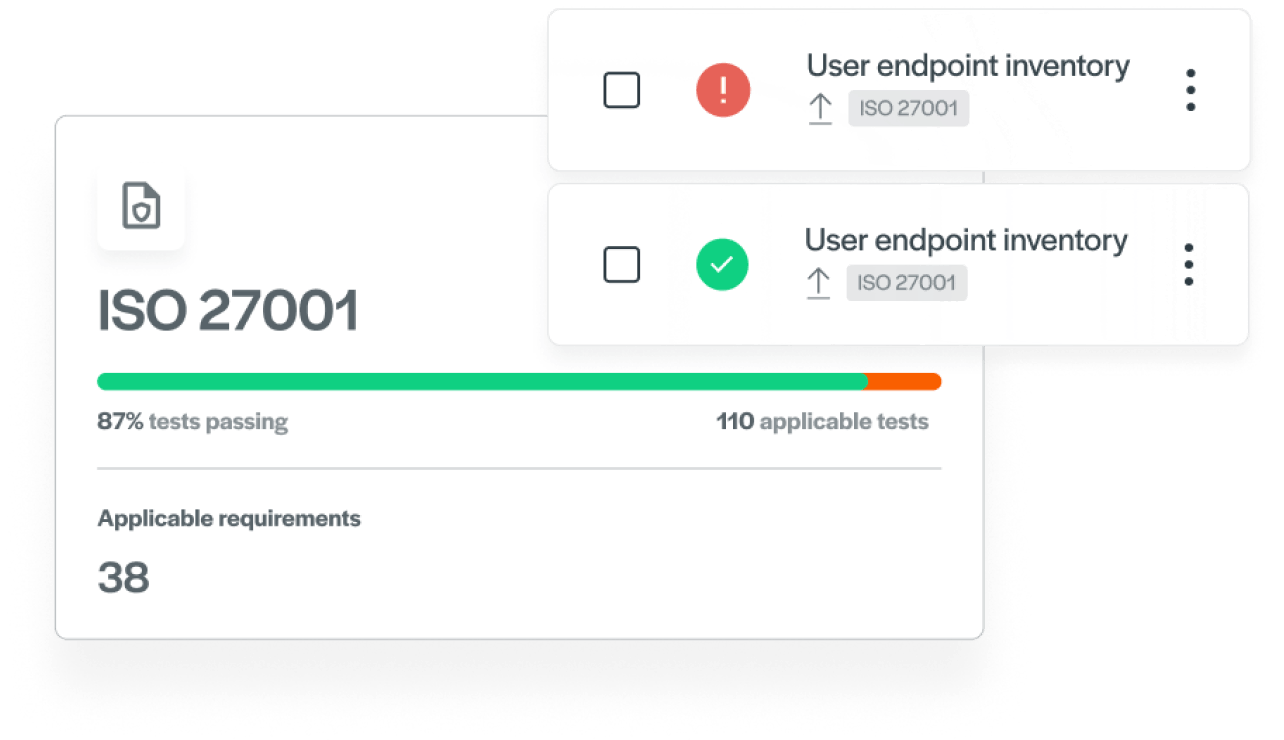
Automate ISO 27001 compliance
Achieve and maintain ISO 27001 certification so you can focus on growing your business globally.
Schedule a demo
Achieve and maintain the global standard for information security
ISO 27001 is a universal standard built for organizations around the globe. ISO 27001 pushes organizations to establish, maintain, and continually improve their information security management system (ISMS) to boost customer confidence.
The ISO 27001 certification lifecycle involves the following:
Initial Certification - Stage 1
Auditor reviews ISMS documentation to ensure the right policies and procedures are in place.
Initial Certification - Stage 2
Auditor reviews business processes and security controls to prove your ISMS meets ISO 27001 requirements. Passing Stage 2 results in an ISO 27001 certification, which is valid for 3 years.
Surveillance Audit 1 and 2
Evaluate your ISMS and a sample of your controls. Two surveillance audits; one each subsequent year following initial certification.
Recertification Audit
The recertification audit occurs during the year of ISO 27001 certificate expiration. Similar to Stage 2, this audit evaluates the evidence to prove your ISMS and controls are effective, and that they meet the ISO 27001 requirements. Passing a recertification audit will renew the ISO 27001 certification period for the next 3 years.
Seamless ISO 27001 Compliance
ISO 27001 has hundreds of requirements to comply with. Save hundreds of hours achieving compliance while enabling best-in-class security practices.
All-in-one compliance automation
Create your policies, train your employees, secure your cloud, and manage risks all in one platform.
Dedicated audit support
Make sure you get your ISO 27001 certificate with guidance from our team of experts.
Continuous monitoring
Ensure you have the right controls in place to maintain compliance.
We’re ready to help
Maintain your ISMS
Design an information security management system (ISMS) that aligns with both the ISO 27001 framework and your organization’s goals. Select from our library of policy templates, adapt them for your organization and publish to your employees—all through the Secureframe platform.
Key benefits
- Access dozens of policy templates developed and vetted by in-house security experts and former auditors
- Easily publish to your employees for review and acknowledgment through the Secureframe platform
Scan and secure your cloud infrastructure automatically
Connect and monitor your cloud infrastructure for ISO 27001 compliance. Plus, no need to install agents — we scan through read-only access.
Key benefits
- Monitor cloud services including AWS, Google Cloud and Azure
- Review vulnerabilities through our dashboard with associated risk scores and details
Assess and manage vendor risk
We make it simple for you to complete vendor risk assessments, regularly review vendors and complete required due diligence.
Key benefits
- Perform and manage vendor risk assessments
- Store, manage and review vendor security certifications and reports for SOC 2, ISO 27001, PCI DSS, CCPA and GDPR
Easily onboard and offboard your employees
Our workflows streamline the onboarding and offboarding process for your employees. Easily track that your designated in-scope personnel have completed background checks, security awareness training and acceptance of security policies — all through our employee dashboard.
Key benefits
- Accelerate employee onboarding with our automated self-serve process
- View employee progress across all assigned tasks through our reports and dashboards
Stay compliant with continuous monitoring and automated evidence collection
Maintain ISO 27001 certification by continuously monitoring your compliance environment and notifying personnel when regular tasks are due. Ensure security, privacy, and compliance requirements are being met with real-time alerts on nonconformities across your tech stack — so that you can fix them quickly.
Key benefits
- Automatic control testing via continuous configuration data collection from 150+ integrations
- Seamless auditor evidence collection workflows and fieldwork processes

“I would definitely recommend Secureframe. Secureframe was instrumental in helping us get SOC 2 and ISO 27001 certified. We always felt like we were talking to experts in the field. Compared to other competitors, choosing Secureframe is a no brainer."
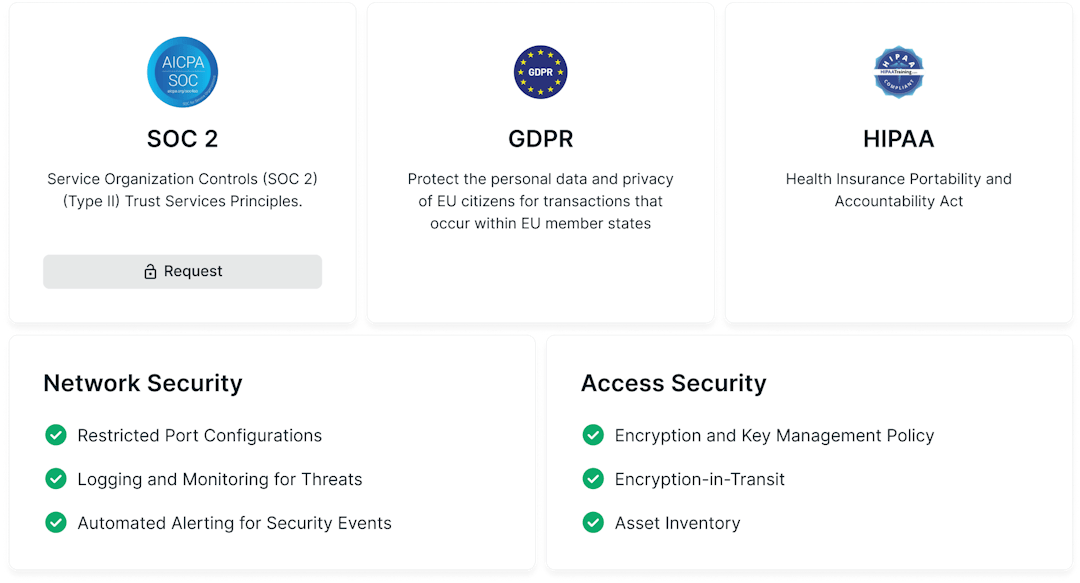
Easily unlock new frameworks
Secureframe’s automated compliance platform has a common control layer that makes it easy to apply the same controls you have completed to additional frameworks, so you can save time meeting new standards.
Obtaining ISO 27001 compliance gives you a jumpstart to these other frameworks with Secureframe-authored common controls:
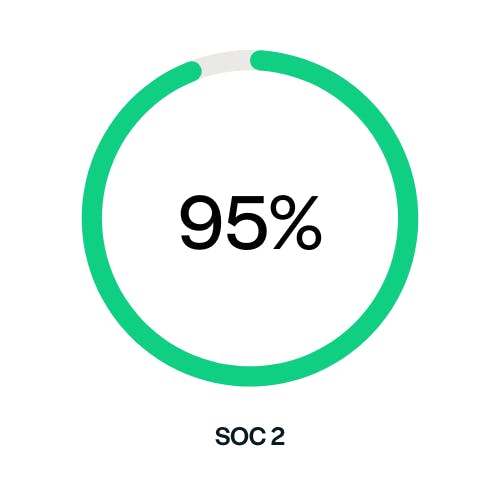 Over 95% SOC 2
Over 95% SOC 2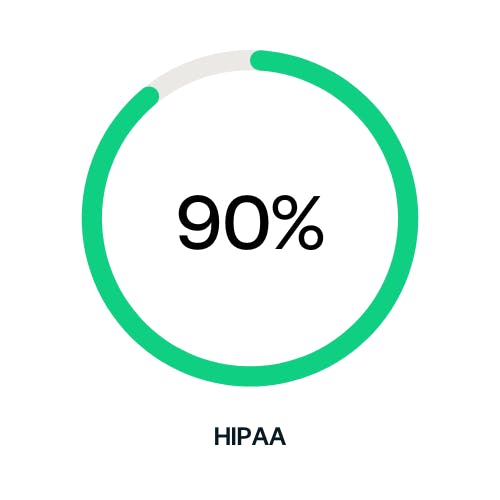 Over 90% HIPAA
Over 90% HIPAA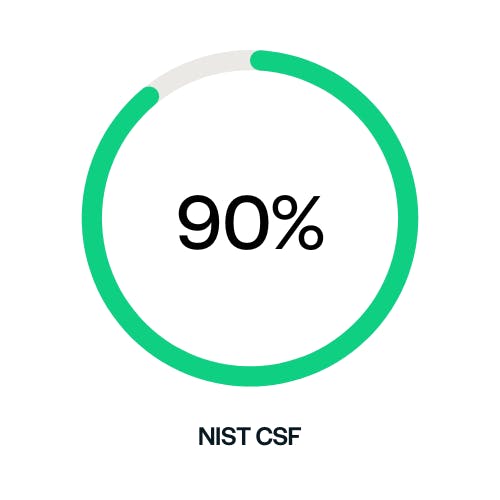 Over 90% NIST CSF
Over 90% NIST CSFLet’s get started together
The Ultimate Guide to ISO 27001
Learn the fundamentals of the ISO 27001 standard and get a step-by-step breakdown of the audit process to help you achieve ISO 27001 certification.
End-to-end compliance right at your fingertips
Automated tests, continuous monitoring, and risk management with the support you need — all in one place.