Request a personalized demo of Secureframe to automate your SOC 2 compliance
With a streamlined SOC 2 workflow and expert guidance, Secureframe automates the entire SOC 2 compliance process, end-to-end. Let’s explore how Secureframe can fit your exact needs.
What we’ll cover:
- Automating the audit readiness process
- Guided support from real, in-house experts
- Maintaining compliance while you scale
- Flexible pricing and plans for any size company
For general questions visit our Help Center.
Powerful SOC 2 security that’s seamless and easy to use
Connect
your tech stack through our integrations
Scan and monitor
your cloud, vendor, and HR ecosystems
Provision
your security systems to be compliant
Continually prove
and maintain SOC 2 compliance
SOC 2: Today’s security standard
SOC 2 reports on your internal controls across five areas: security, availability, confidentiality, processing integrity, and privacy
There are two types of SOC 2: Type I and Type II.
SOC 2 Type I
1 day
Assesses the design of security processes at a specific point in time.
SOC 2 Type II
3 - 12 months
Assesses the effectiveness of security processes by observing operations for at least three months. 6 - 12 months recommended.
How it works
The average SOC 2 has over 200 security requirements to implement. We’ve simplified them into eight key steps—saving you hundreds of hours and delivering best-in-class security.
Meet your dedicated account manager
Scan and secure your cloud infrastructure
Create your compliance policies
Easily onboard your employees
Assess and manage vendor risk
Secureframe SOC 2 readiness assessment
Complete a SOC 2 audit
Continually maintain SOC 2 compliance
Scan and secure your cloud infrastructure
We connect with, monitor, and help provision your cloud infrastructure to be SOC 2 compliant. Plus, no need to install agents — we scan through read-only access.
Key features

Assess and manage vendor risk
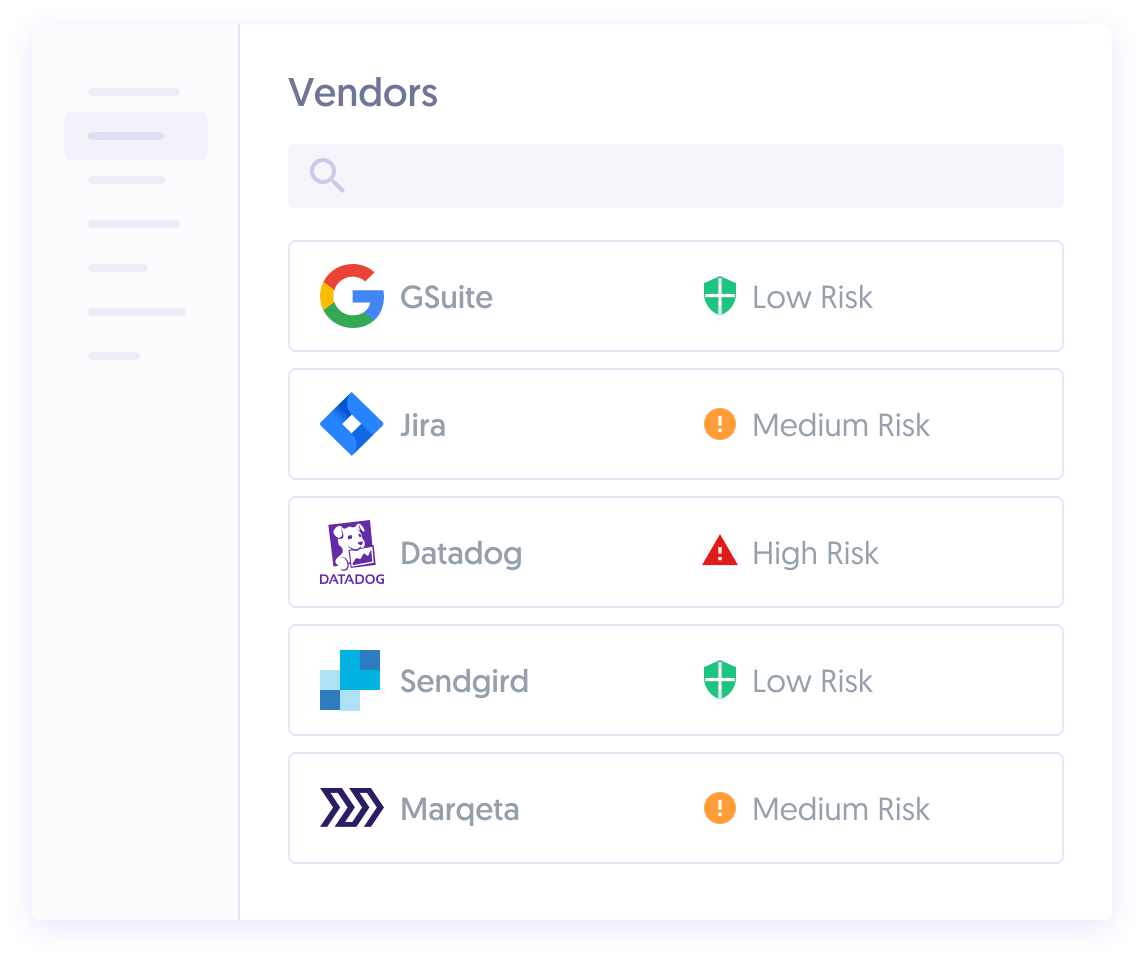
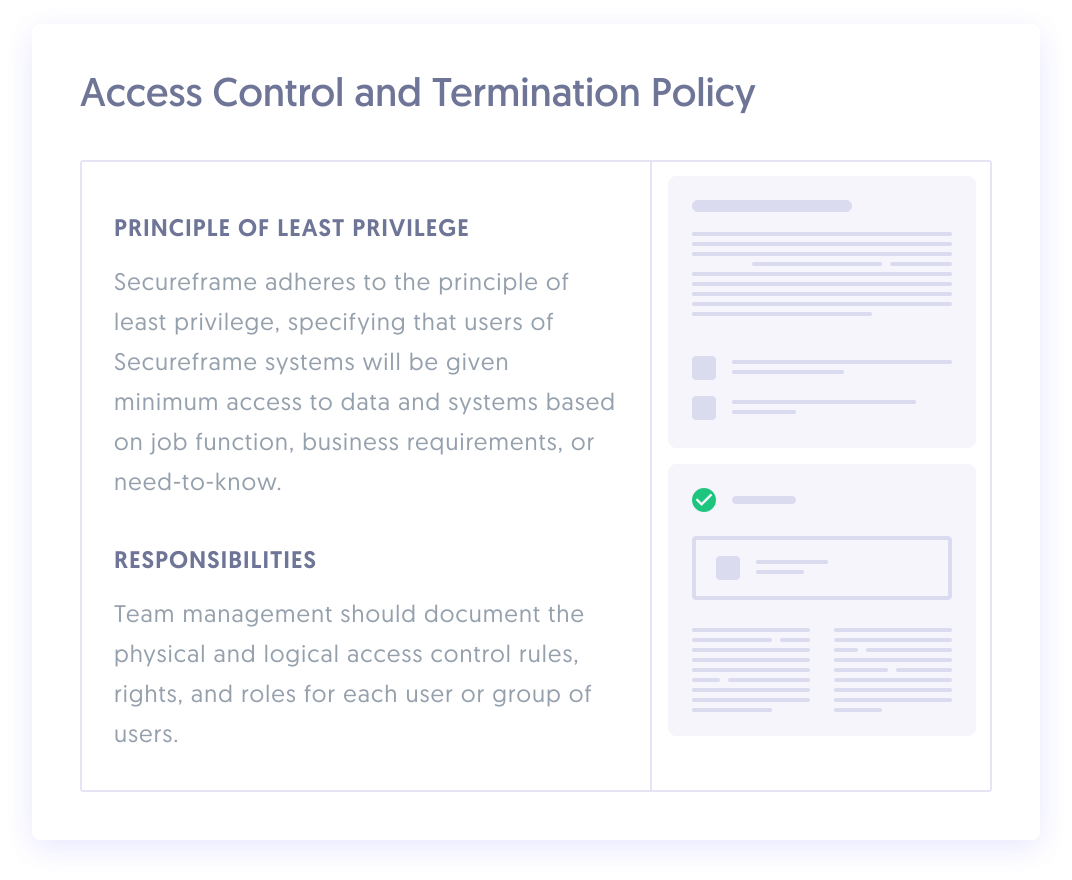
Build your own compliance policies
We help you design SOC 2 security policies that are right for your business. Select from our library of policies, adapt them for your organization, and publish to your employees — all through our portal.
Key features
- 40+ policies developed by compliance experts
and vetted by dozens of auditors - Easily publish to your employees for review
through our portal
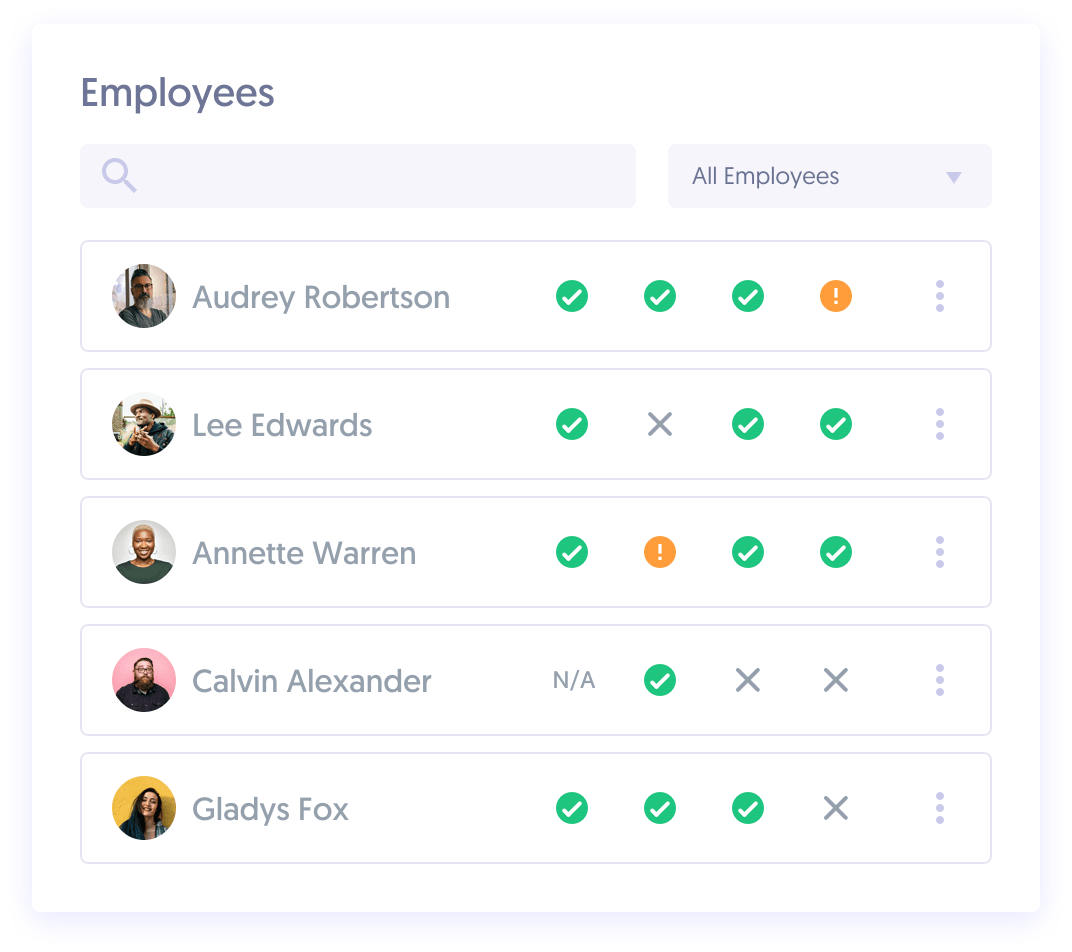
Easily onboard and offboard your employees
Our workflows streamline the onboarding process for your employees. Easily track that your team has completed background checks, security awareness training, and acceptance of security policies—all through and progress dashboard.
Key features
- Employee self-serve through an automated onboarding flow
- Employee progress reports across key
security areas
Stay compliant with automated evidence collection
We help you maintain SOC 2 compliance by automatically collecting evidence throughout the year. Stay secure with real-time alerts on non-conformities throughout your tech stack — so that you can fix them quickly.
Key features
- Automatic evidence collection from 100+ integrations
- Seamless evidence submission workflow with auditors
