At the heart of HIPAA compliance lies one overarching goal: to secure protected health information (PHI).
But how do individual employees ensure they’re safely handling PHI in their day-to-day roles?
Enter: HIPAA policies and procedures.
Businesses must create and implement a set of policies and procedures that break down the complex HIPAA rules into instructions that are simple to understand and follow.
Below, we cover what HIPAA policies and procedures look like, examples of necessary policies, and how to create your own.
What are HIPAA policies and procedures?
The HIPAA law was passed in 1996 and was created to safeguard PHI, which includes everything from your name and address to prescriptions and test results.
To ensure businesses are protecting PHI properly, employees must follow specific instructions. This is where HIPAA policies and procedures come into play.
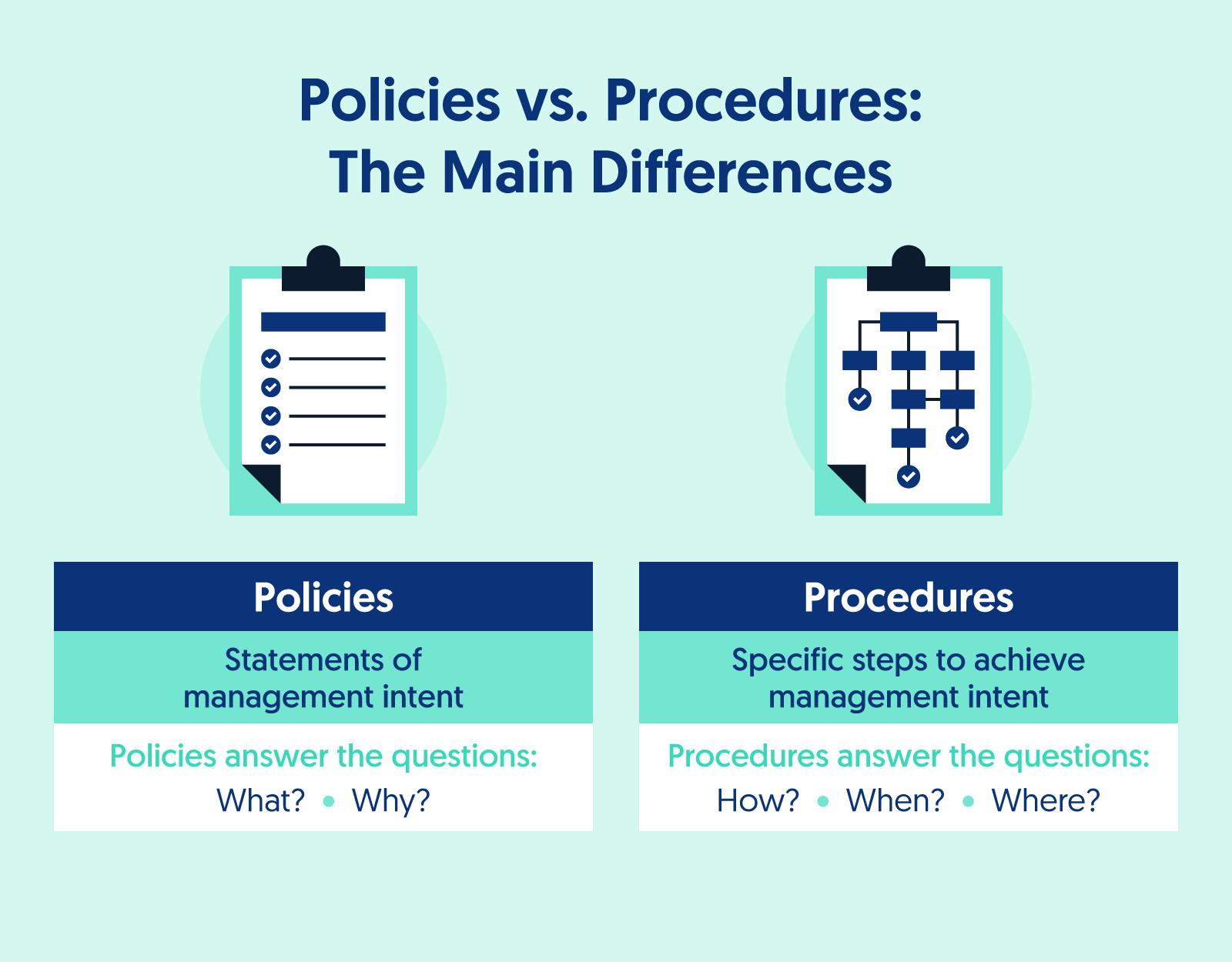
- Policy: A policy is a statement of management intent. They answer questions about what employees must do and why they must do it.
- Procedure: A procedure includes specific instructions for how to achieve management intent.
Policies and procedures are essential to HIPAA compliance — and are required by HIPAA law. Failure to develop and implement policies and procedures is a HIPAA violation, which can lead to financial and criminal penalties.
Why are policies and procedures necessary?
Aside from being required by law for HIPAA compliance, policies and procedures offer additional benefits for organizations, including:
- Clarity: Policies and procedures help simplify HIPAA’s complex regulatory jargon into documents that are easier to understand for employees.
- Uniformity: Policies and procedures increase the likelihood that employees will pursue the same goals, with the same values, in the same ways across the organization.
- Simplicity: Employees likely don’t have the time to read each of the HIPAA rules. Policies and procedures state the most important information about regulatory requirements that employees need to do their jobs.
Recommended Reading

The Ultimate HIPAA Compliance Checklist for 2022
HIPAA rules
HIPAA outlines a series of rules that organizations must adhere to in order to be HIPAA compliant. A few of the main ones are the Privacy Rule, Security Rule, and Breach Notification Rule.
Below we dig into specific policies that apply to each.
Privacy Rule
The Privacy Rule regulates the use and disclosure of PHI. The rule requires that businesses properly safeguard PHI and gives patients greater control over who can access their medical information.
This HIPAA rule applies to any business that has access to patient information that, if compromised, could harm a patient’s finances or reputation or result in fraud.
The Privacy Rule is enforced by the Department of Health and Human Services Office of Civil Rights (OCR), state attorneys general, and Centers for Medicare and Medicaid Services (CMS).
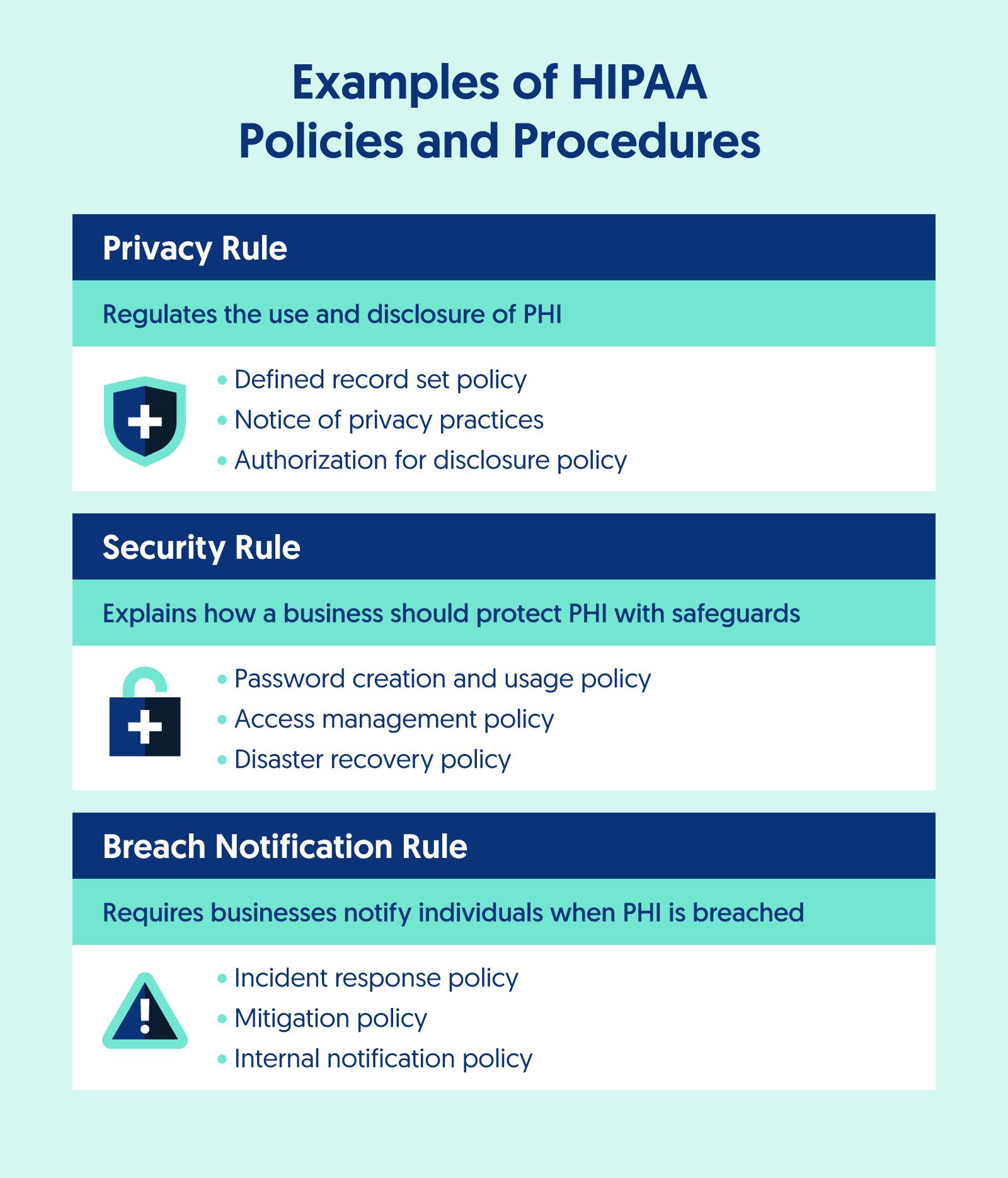
Examples of policies and procedures under this rule include:
- Defined record set policy
- Notice of privacy practices
- Authorization for disclosure policy
- Minimum Necessary Requirement policy
- Record retention policy
- Workers’ compensation policy
- Confidential communications policy
Security Rule
The HIPAA Security Rule explains how businesses should safeguard PHI.
Under the Security Rule, there are three types of safeguards to protect patient information from breaches.
- Administrative safeguards explain what the organization does to protect PHI.
- Physical safeguards aim to protect physical assets from unauthorized access.
- Technical safeguards define how the organization will handle electronic protected health information (ePHI).
Additionally, businesses need to practice risk management and conduct risk assessments to ensure that the PHI is secure.
Examples of policies and procedures under this rule include:
- Access management policy
- Automatic logoff policy
- Data backup and retention policy
- Device and media controls policy
- Disaster recovery policy
- Facility access control policy
- Information systems computer management policy
- Internet and computer usage policy
- Intrusion detection policy
- Password creation and usage policy
- Risk management policy
Breach Notification Rule
The Breach Notification Rule requires organizations to notify affected individuals and the Department of Health and Human Services (HHS) when unsecured PHI has been breached.
To avoid a fine from the OCR, organizations must send notifications to affected individuals within 60 days of the breach being identified.
Notifications must explain what happened, what information was compromised, how the business is responding to the breach, and how it will prevent future breaches.
Examples of policies and procedures under this rule include:
- Incident response policy
- Mitigation policy
- Internal notification policy
Policies and procedures for business associates
Business associates are third parties that a covered entity shares PHI with. There are certain policies and procedures required by HIPAA to ensure that these third parties are also doing their part to protect PHI.
This includes a contract stating the acceptable and unacceptable uses of PHI by the third party known as a Business Associate Agreement (BAA). Businesses should also create policies and procedures to monitor these relationships over time, corrective actions in the event of a breach, and termination.
Recommended Reading

What Is a HIPAA Business Associate Agreement? [Free Template]
How to manage your HIPAA policies and procedures
We explain the process of creating and managing your HIPAA policies and procedures below.
Write out your policies and procedures
Policies and procedures include three key elements: the purpose, the scope, and the procedures.
- Purpose: Policies and procedures are written for a particular reason or purpose. This purpose should be explained at the beginning so the reader knows why the policy was created.
- Scope: A policy should also include the scope, or who the policy applies to. If the policy is meant for every employee, that should be stated within the document. If the policy applies to certain situations, that should also be stated.
- Procedures: Policies include procedures, or the specifics of how a business will achieve the policy intent. These are the step-by-step actions employees must take to meet the HIPAA requirement the policy is designed around.
To design effective procedures, simplify the language and remove any complex HIPAA jargon to make it easier for employees to understand.
Share policies and procedures with your team
Once policies and procedures have been written, your team needs to be able to understand and share them. Keep these policies somewhere that employees can easily access them, such as a company knowledge base.
Train your staff on HIPAA compliance
It’s not enough to share these documents with your staff. You must also provide HIPAA training to help them better understand the organization's policies and procedures and how they relate to their role and responsibilities.
Develop a review and approval process
To ensure your policies and procedures stay up to date, your business should appoint a team to regularly review, approve, and finalize any changes or updates to policies and/or procedures. When changes have been made they should be noted within the policy’s version history.
When changes occur, a business may need to do refresher trainings with their staff or update their BAAs. All HIPAA policy changes must be documented and maintained for a minimum of six years.

How Secureframe can help you streamline HIPAA policy and procedure creation
Creating policies and procedures from scratch can feel overwhelming — especially with the number of policies you need for HIPAA compliance.
Secureframe can help you simplify the entire process by providing you with policy templates that can be tailored to the specific needs of your organization.
To learn more, request a demo with our team today.
FAQs
What policies are needed for HIPAA?
Here is a list of key policies that are typically needed for HIPAA compliance:
- Privacy Policies:
- Notice of Privacy Practices: Policies regarding how PHI is used and disclosed, and informing patients of their rights regarding their health information.
- Patient Rights: Policies outlining the process for patients to access their PHI, request amendments, and account for disclosures, among other rights.
- Minimum Necessary Use and Disclosure: Policies that ensure PHI is only accessed and disclosed to the minimum extent necessary to accomplish the intended purpose.
- Security Policies:
- Risk Analysis and Management: Policies for conducting regular risk assessments and implementing measures to mitigate identified risks to the security of PHI.
- Data Encryption: Policies detailing when and how PHI should be encrypted, both at rest and in transit.
- Access Control: Policies that define who can access PHI, how access rights are granted, reviewed, and terminated, and how access is controlled and monitored.
- Physical Security: Policies and procedures to safeguard facility access and protect equipment containing PHI from unauthorized access, tampering, and theft.
- Workstation and Device Security: Policies governing the use and security of workstations and electronic devices that access PHI.
- Security Incident Response and Reporting: Policies for identifying, responding to, and documenting security incidents and breaches.
- Breach Notification Policies:
- Breach Identification and Response: Policies outlining the process for identifying, responding to, and mitigating the effects of a PHI breach.
- Notification Procedures: Policies detailing how and when to notify affected individuals, the HHS, and potentially the media in the event of a breach involving PHI.
- Employee Training and Management:
- Training: Policies requiring regular training for all employees on HIPAA regulations and the organization's privacy and security practices.
- Sanctions: Policies detailing disciplinary actions for employees who fail to comply with HIPAA regulations and the organization's policies.
- Business Associate Management:
- Business Associate Agreements: Policies for entering into agreements with business associates that ensure they appropriately safeguard PHI under HIPAA requirements.
- Complaints and Compliance:
- Complaints Process: Policies establishing a process for receiving and addressing complaints concerning the organization's privacy practices.
- Compliance Auditing and Monitoring: Policies for regular internal audits and monitoring to ensure ongoing compliance with HIPAA regulations and the effectiveness of the implemented policies.